Microsoft has released a 948-page document which contains documentation on over 250 windows console commands. The document may be found on GitHub but is also available for direct download at https://www.microsoft.com/en-us/download/details.aspx?id=56846 .
 Recently the Australian prime-minister made world news for his stance on the going dark debate. According to Prime Minister Malcolm Turnbull Information Technology giants like Facebook, Google and Apple should work with law enforcement to decrypt encrypted messages to aid in the fight against crime and extremism. Turnbull ruffled feathers by boldly stating that “though the laws of mathematics are very commendable, the only law that applies in Australia is the law of Australia”. He further opened himself up to ridicule from the tech community by giving an incorrect definition in his answer to one reporter’s question of what is a backdoor?”.
Recently the Australian prime-minister made world news for his stance on the going dark debate. According to Prime Minister Malcolm Turnbull Information Technology giants like Facebook, Google and Apple should work with law enforcement to decrypt encrypted messages to aid in the fight against crime and extremism. Turnbull ruffled feathers by boldly stating that “though the laws of mathematics are very commendable, the only law that applies in Australia is the law of Australia”. He further opened himself up to ridicule from the tech community by giving an incorrect definition in his answer to one reporter’s question of what is a backdoor?”.
Even more recently, Equifax, one of three major US credit reporting companies reported a data breach which may affect 44% of the US population approximately 143 million US customers. At the time of writing, there are reports that thousands of Canadians may also be among those affected. According to details released by Equifax, hackers were able to access customer PII including but not limited to their full names, addresses, and SSNs. Given the quality and quantity of this breach, the opportunities for exploitation through social engineering and other means seem endless.
This article though is not about bashing or shaming Prime Minister Turnbull for his stance on the laws of mathematics or his incorrect representation of what is a backdoor. It is not even an avenue to vent outrage at Equifax for not doing a better job at protecting such sensitive information; although I know many would not fault me if it were.
Instead, it is a call to professionals in the field to own our area and to take responsibility for leading the discourse and effort needed to build structures which will support the impact of technology in our society. This includes pillars of policy and regulation around privacy, security, and safety. As professionals, we have an intimate understanding of many of the issues present and impending and we need to be the voice that ensures we don’t just have a discussion but that it is focused and steered in the right direction.
In response to Prime Minister Turnbull – the going dark debate is not a new one and both sides of this debate have merit. It is unreasonable however to expect that technology be stifled and its growth inhibited in the name of law enforcement. The need and value of law enforcement cannot be discounted but certainly, we are advanced enough in thought and technology to find a solution to this hurdle – to use technology to enable our law enforcement rather than encumber it.
Additionally, the laissez-faire approach to handling sensitive information and the Equifax breach are merely symptoms of our flawed system. They highlight where our value system lies: in profits rather than integrity and we will continue to see this happen again and again unless we do something radical to prevent it.
So will the real information security professionals please stand-up?
Will we be the voice needed to hold our governments accountable for legislation that will not stifle technology but nurture it, will we shout about the need to hold corporations accountable for the care of our personal information? Will we offer advice on how these regulations should be implemented to ensure organizations which are found culpable are also held responsible?
Or will we stand by and have decision after decision made without our expertise and input while we whisper and then complain about their inadequacy, only after the fact?
Will the real information security professionals please stand-up?
Spear phishing attacks
A variant of the phishing attack typically executed against a restricted group of selected targets. Usually, it uses email-spoofing fraud to exploit a particular organization, seeking unauthorized access to sensitive data. Spear phishing, unlike a basic phishing attack, doesn’t address a wide audience and is conducted by attackers that are more interested in intellectual property, trade secrets, or military information rather than financial gain. Typically spear phishing attacks are conducted by state-sponsored hackers and by hacktivists that search for reserved information for various reasons [1].
Whaling attack
Another evolution of phishing attacks that utilizes sophisticated social engineering methods to acquire confidential information, personal data, access credentials to restricted services/resources from executives of private business and government agencies. The word whaling is used, indicating that the target is a big fish to capture [2].
In a 2008 FBI subpoena, it was reported that around 20,000 corporate CEOs were attacked with this technique. They received emails that asked them to download a “special” browser add-on to view the entire subpoena document. The link proposed allowed the download of a keylogger that secretly captured passwords. As a result, the compromised companies were victims of further cyberattacks with serious consequences [2].
Water Holing
This attack is quite similar to whaling, however, there are two distinct differences:
- The target is often a group or specific organization, not an individual.
- Rather than sending an email, the perpetrator is likely to infect a website which the target is known to frequent for example if the target is medical doctors, the website infected may be doctors.org, a site where doctors frequent for training, networking or other reasons.
Once the website has been compromised it is infected with malware so that visitors to the site eventually become infected during the course of their visit. Water holing schemes are often quite expensive to plan, prepare and execute this explains why they are usually attacks which target organizations and groups.
References
- Mc Afee, “McAfee Labs,” August 2014. [Online]. Available: http://www.mcafee.com/ca/resources/reports/rp-quarterly-threat-q2-2014.pdf.
- J. Chhikara, R. Dahiya, N. Garg and M. Rani, “Phishing & Anti-phishing Techniques: Case Study,” International Journal of Advanced Research in Computer Science and Software
There are a wide variety of methods uses to perpetrate phishing attacks, some of which include:
- Email / SpamWeb Based Delivery
- Instant Messaging
- Session Hacking
- Trojan HostsLink
- System Reconfiguration
- Content Injection
- Phone Phishing
- Malware Phishing
- Key Loggers
CURRENT TRENDS IN PHISHING
Initially, phishing was categorized as a type of spam, however due to current trends in phishing attacks it has emerged has a category of cyber-attack that can stand on its own. In fact, there are now many variants of phishing attacks which will be discussed in following articles and according to [1] email has been surpassed as the most common distribution instrument for phishing attacks. Links followed while web browsing and using messaging systems such as skype, account for over 80% of registered phishing attacks.
THE PHISHING PROCESS
Executing a phishing attack has a few stages, the following is a common approach used:
- The attacker obtains the e-mail addresses of the intended victims.
- The attacker generates an email that appears genuine and requests the email recipient to perform some action.
- The attacker sends the email to the intended victims in a way that seems to be legitimate, obscuring the true source.
- Depending on the content of the email, the recipient opens a malicious attachment, completes a form, or visits a web site.
- The attacker stores the victim’s sensitive information and exploits it for some kind of gain.
CONTEMPORARY PHISHING ATTACKS

The increase in the use of technology has also resulted in the increase in the number of methods and platforms used to execute phishing attacks. The following are a lists of common variations of traditional phishing attacks:
SMiShing
Definition: A form of Phishing that uses short messaging services (SMS) or text messages on mobile devices as a means of gather information that will then be used to exploit the victim.
Fishing usually involves the dangling of bait in a substantial body of water to entice and attract fishes to bite. When a fish take the bait, it usually gets reeled in at great personal cost, quite often its life.
Similarly, phishing is a social engineering attack in which users are tricked into biting the bait and revealing personal information which may result in identity theft, financial loss and compromised confidentiality of information. The most common baits used in phishing attacks are emails and websites; claiming to represent legitimate enterprises, making sincere requests to the unsuspecting email reader or web surfer. The next few articles in this series will define and describe the variety of attack categorized as phishing while examining some of the most common anti-phishing techniques used to mitigate these types of exploits.
Statistics show that phishing attacks though simple in design have increased exponentially in recent years. Continue reading “PHISHING – Part 1”
The United States National Institute of Standards and Technology’s (NIST) defines cloud computing as: “a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or service provider interaction.” C.I.A Bytes puts it this way, in traditional computing the computer and its peripherals such as
C.I.A Bytes puts it this way, in traditional computing the computer and its peripherals such as keyboard, printer and hard drive combine to perform a series of inputs, outputs, processing and storage while being physically located in the same space or very close proximity. In the cloud computing environments it is quite similar, the key difference being that the storage device(s) and often processing are no longer located in the same place as the input and output peripherals, thus a network interface becomes necessary to provide access to data assets held on the storage device(s). There are three categories of services, offered by the Cloud: Infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (SaaS).
IV. The Debate
The increase in the strength of encryption offered by Apple and Google have been viewed as a response to Edward Snowden’s public revelation of just how much the government infringes on the perceived privacy of its citizens. Companies thus felt a need to reassure their customers that they value their right to privacy and were willing to go to certain lengths to convey this message [8]. One may argue that according to the provisions set out in CALEA, the tech giants are well within their rights to do so since they are in fact not breaking any laws by implementing technology to ensure more secure mobile communications.
On the other hand “Law enforcement officials have likened the new encryption to a house that can’t be searched or a car trunk that could never be opened [8]”, testimony from employees of the FBI describe cases in which access to smart phone data were instrumental in cracking criminal cases, often involving kidnappings and murder [5] , thus a grim picture is painted of the inability to decrypt data during investigations – one of criminals running wild and free, outsmarting law enforcement officials.
In contrast some security experts feel that the government is being hysterical [2], that the amount of criminal investigations which have been frustrated by the inability to decrypt information is marginal at best, and according to statistics provided by [3], this in fact seems to be the case, see fig1.
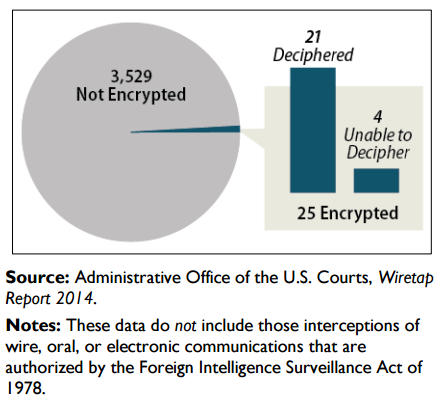
Fig 1 – Authorized wiretaps which encountered encryption in 2014[9]
Continue reading “Strengthened Mobile Data Encryption and Law Enforcement – Part 2”
There are times when technology can create a great deal of tension challenging the status quo and effecting immediate change.
This post takes a look at the effect of encryption on law enforcement both historically and most recently with the announcement by Google and Apple Inc: to strength mobile data encryption by providing default encryption mechanisms for users of both the Android and iOS operating systems. It explores the alarming response to this announcement by American law enforcement agencies and examines whether or not there is merit in the disturbing picture painted by law enforcement of investigations being foiled by the government’s inability to decrypt communications.
I. Introduction
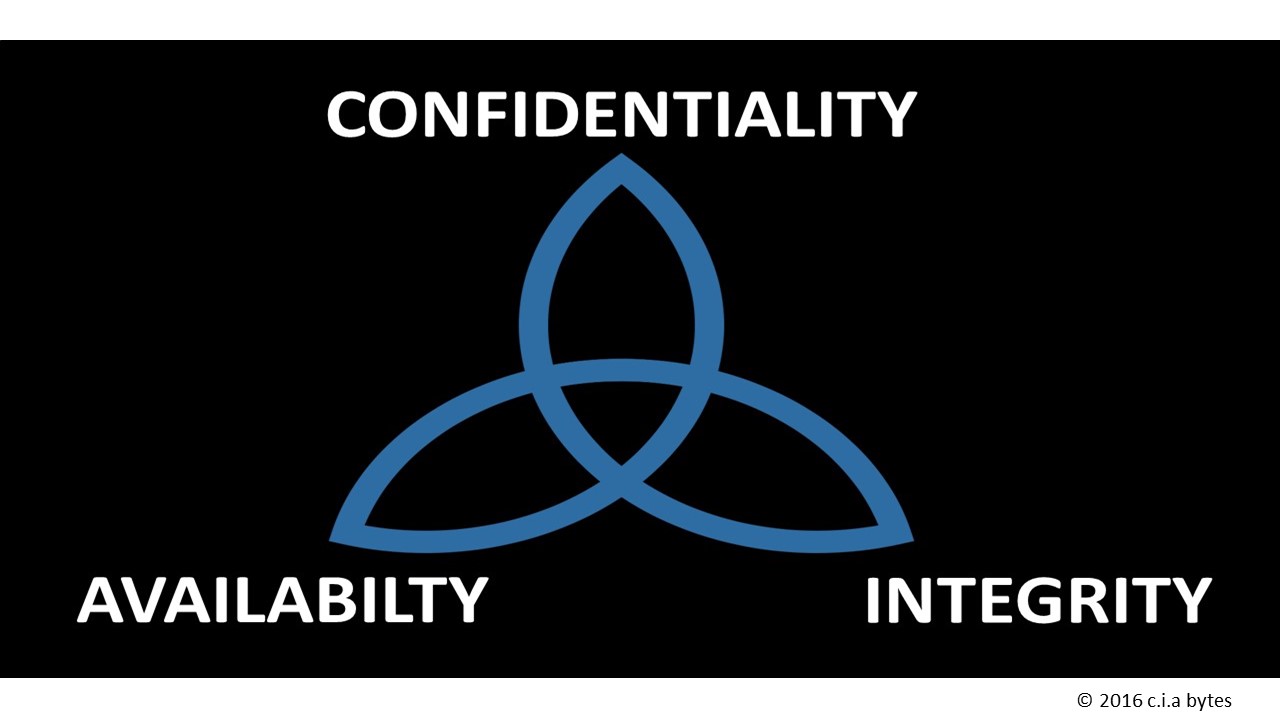
The CIA triangle represents the foundational goals of Information Security: Confidentiality, Integrity and Availability; Cryptography is used to primarily provide the first of this triad – Confidentiality. Cryptography involves the use of ciphers (encryption algorithms) to encipher and decipher messages so that only the intended recipient is able to gain access to the encrypted message. In practice, cryptography is susceptible to many types of attacks however modern cryptographic methods have evolved from Caesar and Vigenère ciphers to algorithms which are extremely difficult to break. Today’s “strong encryption” requires the use of super computational power to crack and even then the amount of time needed to break these ciphers, often make the job unthinkable and unachievable in this lifetime; this presents a challenge to law enforcement organizations.
This post is structured as follows: section II briefly describes the encryption methods used by Apple’s IOS and Google’s Android operating systems, the two market leaders in the mobile operating system market. It also highlights the changes, to mobile data encryption announced by both vendors in 2014 and the concerns which resulted in regard to law enforcement. Section III sheds some light on the history of law enforcement and strong encryption, detailing some of the measures taken historically by the US Government to assist law enforcement agents with the challenges of encryption technology. Section IV provides an analysis of both sides of the strong encryption debate and highlights some possible strategies in balancing the use of strong encryption and the needs of law enforcement. Section V provides a brief summary and thus concludes the paper.
II. The Buzz
A. Software encryption used by iOS and Android
In September 2014, Apple announced its decision to change the way it would encrypt data present on its devices using Apple’s iOS, with the release of the new version of iOS – iOS8. Prior to this announcement, devices running on iOS offered encryption however the encryption only protected a small amount of the data found on the device and Apple was able to bypass the security features on the rest of the data resident on the mobile phone [2].
B. Changes to iOS and Android
The announced update to iOS8 saw the encryption of all mobile data, which is protected by a user’s passcode [3]. This essentially took any power out of the hands of Apple, that is, Apple could no longer bypass a user’s passcode and gain access to the encrypted data, thus it became pointless for law enforcement agents to request access to mobile data via wiretap orders to Apple, as had been previously done.
To compound the issue, a few days after Apple’s announcement, Google: creator of the Android operating system, which is the world’s most popular smart phone OS [4] announced their decision to follow the trend set by Apple. According to Google their latest release of the Android OS – Android 5.0: the L-release, would offer default enabled encryption; files then would only be viewable by someone entering the device password. Keys to the encryption and decryption ciphers would not be stored outside of the device by Google, so, like Apple wiretap orders served by law enforcement officials to the Tech giant for access to data on Android devices would be impossible to fulfill [4].
C. What this means for law enforcement
“Going dark” refers to the incapability of law enforcement authorities to decipher encrypted forms of communication while carrying out criminal investigation as technology continues to evolve. The announcement of updated encryption settings by Apple and Google has brought this lack of capability to the forefront.
The problem is not that law enforcement agents are unable to access data but that even when data is accessed the information cannot be deciphered and so becomes unusable, frustrating the investigation process. According to testimony by [5], the Executive Director of the Science and Technology Branch of the FBI, although mobile data encryption is not new, the recent announcements by Apple and Google put a new spin on the problem: “ previously encryption had to be selected by the user now it is turned on automatically, requiring no affirmative action by the consumer ”.
Continue reading “Strengthened Mobile Data Encryption and Law Enforcement – Part 1”
The C.I.A – no not the Central Intelligence Agency, but CONFIDENTIALITY, INTEGRITY AND AVAILABILITY perhaps the three most important tenants of Information Security.
Confidentiality – Is the information meant for your eyes?
Confidentiality looks to the issue of authorization, ensuring information confidentiality means ensuring that the person or system accessing information is the authorized to do so; thus, without authorization, there should be no access.
Integrity – Is the information really what it purports to be?
Integrity speaks to the issue of trust: that what is being represented is what was intended. Information that has been modified intentionally or unintentionally without authorization loses its integrity. There should be controls in place to prevent this or at the very least detect such unauthorized modifications.
Availability – Is the information accessible to those who are entitled to it?
Availability looks at access to information, it is a waste of time, money and other resources to prevent access to information by legitimate users, in contemporary information systems it is common to make provisions for redundancy and information recovery in the event of incidents or disasters which threaten the availability of information.
In today’s age of information, when info-sec practitioners develop policies, standards, procedures and implement controls, it is always with the intent of preserving the confidentiality, integrity and or availability of information.