IV. The Debate
The increase in the strength of encryption offered by Apple and Google have been viewed as a response to Edward Snowden’s public revelation of just how much the government infringes on the perceived privacy of its citizens. Companies thus felt a need to reassure their customers that they value their right to privacy and were willing to go to certain lengths to convey this message [8]. One may argue that according to the provisions set out in CALEA, the tech giants are well within their rights to do so since they are in fact not breaking any laws by implementing technology to ensure more secure mobile communications.
On the other hand “Law enforcement officials have likened the new encryption to a house that can’t be searched or a car trunk that could never be opened [8]”, testimony from employees of the FBI describe cases in which access to smart phone data were instrumental in cracking criminal cases, often involving kidnappings and murder [5] , thus a grim picture is painted of the inability to decrypt data during investigations – one of criminals running wild and free, outsmarting law enforcement officials.
In contrast some security experts feel that the government is being hysterical [2], that the amount of criminal investigations which have been frustrated by the inability to decrypt information is marginal at best, and according to statistics provided by [3], this in fact seems to be the case, see fig1.
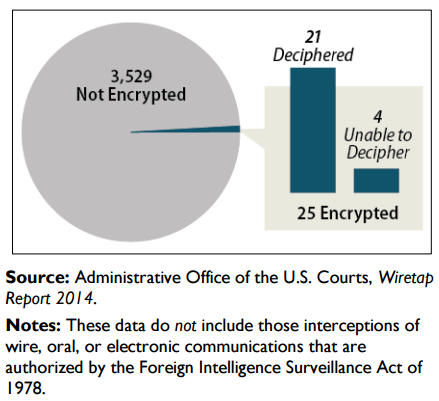
Fig 1 – Authorized wiretaps which encountered encryption in 2014[9]
2) Analysis
Both sides in this debate have merit, it is unreasonable however to expect that technology be stifled and its growth inhibited in the name of law enforcement. The need and value of law enforcement cannot be discounted but certainly we are advanced enough in thought and technology to find a solution to this hurdle. The authors of [7] reasoned that rather than looking at the law enforcement – encryption issue as the beginning of “going dark”, we should instead see it as “the golden age of surveillance” and they present a strong case for this stance. Admittedly the use of strong encryption does reduce some traditional methods of encryption, however with advances in technology have come new ways of collecting information and a plethora of new types of information which may be used for investigations [7]. In the 1990’s the idea of tracking an individual’s location precisely using Geographical Positioning Systems was something seen only in the movies, a technology that was still in infancy and considered a military initiative, now many of us woud not be able to get to work without it and it is freely available for law enforcement use.
Additionally the proliferation of smart devices, social media and networking, makes it extremely difficult for individuals to live off the grid, investigators now are able to gather dossiers of information on individuals and groups by examining their online footprints, we have become so reliant on the internet and its services.
Moreover, we can look even closer at the details surrounding Apple’s delivery of services to it’s smart devices, iOS devices are set to sync to a user’s iCloud account, which is Apple’s cloud storage services for owners of apple devices, which incidentally is widely used by customers. This cloud syncing allows not just storage but syncing of content across devices for customers who own several devices thus allowing access to user files regardless of the device being used. According to Apple they no longer have access to the data stored on a user’s phone, however they most certainly have control over the way data is encrypted and stored on the iCloud and are thus able to access it. This means that should Apple be served a court order to provide access to information stored on their cloud, they will in fact be obligated to comply based on the CALEA legislation.
In light of this information going forward, law enforcement and government should work closely to provide training for operational staff to develop and execute new methods of performing digital investigations and surveillance. This is the age of information, there is such a continuous bombardment of data that it is unfathomable that our security agencies are not able to capitalize on this treasure and use it to help secure our communities.
3) V. Conclusion
Having examined the issue of law enforcement and encryption in light of the decision by smart phone OS providers to strengthen encryption, it seems as though there really isn’t as a great a dilemma as many may like to believe, there are still many tools in the hands of law enforcement. Though one cannot deny that the issue does present challenges it is expected that law enforcement like other sectors impacted by technology, must evolve and also strengthen their own methods of surveillance. There are certainly old and new means available to do so. Law enforcement can continue to work closely with private companies driving technology and the government to ensure funding, policy and research are done to further both the cause of national development and national security.
4) VI. References
[1] D. E. Denning, “Encryption and Law Enforcement,” 21 February 1994. [Online].
[2] B. Schneier, “Stop the Hysteria over Apple Encryption,” Schneier on Security, 3 October 2014. [Online]. Available: https://www.schneier.com/essays/archives/2014/10/stop_the_hysteria_ov.html. [Accessed 22 October 2015].
[3] K. Finklea, “CRS Report R44187, Encryption and Evolving Technology: Implications for U.S Law Enforcement Investigations,” Congressional Research Service, 2015.
[4] C. Timberg, “Newest Androids will join iPhones in offering default encryption, blocking police,” Washington, 2014.
[5] A. Hess, “Encryption and Cyber Security for Mobile Electronic Communication Devices,” Federal Bureau of Investigations, 2015.
[6] US General Accounting Office,, “FBI advanced Communications Technologies Pose Wiretapping Challenges,” Federal Bureau of Investigations, 17 July 1992.
[7] P. Swire and K. Ahmad, “‘Going Dark’ Versus a ‘Golden Age for Surveillance’,” Center for Democracy and Technology (https:www.cdt.org), 28 November 2011.
[8] D. Barrett and D. Yadron, “New Level of Smartphone Encryption Alarms Law Enforcement,” 22 September 2014. [Online]. Available: http://www.wsj.com/articles/new-level-of-smartphone-encryption-alarms-law-enforcement-1411420341. [Accessed 23 November 2015].
[9] Administrative Office of the US Courts, “Administrative Office of the US Courts, Wiretap Report 2014,” US Courts, 2014.
Leave a comment